Today’s business landscapes tend to be heterogeneous with interconnected systems and increasing number of mobile and cloud-based applications. This diversity makes it difficult to use traditional approaches to protect assets from internal threats. The amount of security-relevant data generated by systems and applications in today’s landscapes is huge and is spread across a vast number of logs. And for organizations running SAP systems, a further challenge is to gain insights into SAP business systems to identify security risks.
SAP Enterprise Threat Detection
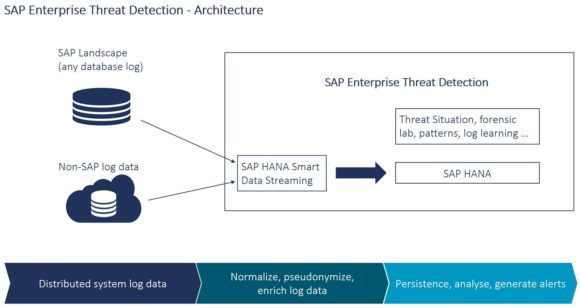
Camelot ITLab handles these challenges through SAP Enterprise Threat Detection (ETD), a native SAP HANA application which SAP designed to protect its own business data. It combines the high-performance complex event processing functionality of SAP Event Stream Processor (SAP ESP) and the real-time capabilities of SAP HANA to create a powerful solution for processing and analyzing security-relevant data. SAP ETD helps security administrators to detect, monitor, and analyze security events to provide insight into what is happening throughout heterogeneous landscapes including SAP and non-SAP systems by scanning log files.
Systems monitored by SAP Enterprise Threat Detection are known as log providers. Log data is extracted and transferred from the log providers to SAP ETD. The SAP ESP engine pre-processes the incoming log data and makes it compatible for SAP HANA, and then sends it to the SAP HANA database, where it is stored. Then, SAP ETD runs attack detection patterns on the log data and generates alerts when suspicious patterns are found. It is all based on a user-friendly SAP Fiori interface.
Data compliance within ETD
The information contained in all alerts such as system, user, or terminal information is very useful for threat analysis. As we make use of only normalized, enriched and pseudonymized information instead of the raw log data, data compliance is not compromised and greatly reduces the amount of information being transferred to the external tool. Camelot ITLab imposes a division of responsibility between those who can access individual’s identities and those who cannot, when legal follow-ups or actions are required for a forensic investigation.
Real-time analysis in ETD
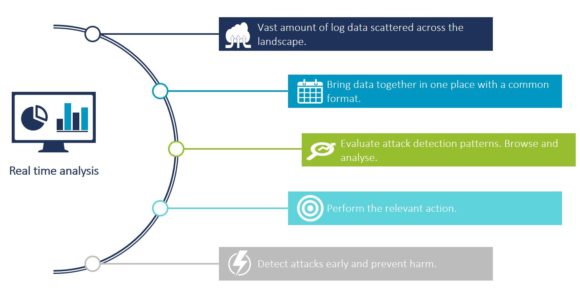
SAP Enterprise Threat Detection allows you to perform real-time analysis and correlation of vast log data regardless of its original source, and it is used as a stand-alone security monitoring solution. It helps you identify the attacks as they happen using real-time data and analyze the threats quick enough to neutralize them before serious damage occurs.
The speed at which ETD analyzes security-relevant log data gives a significant advantage in combating cybercrime. The earlier you can address a threat, the smaller the window for causing damage to your business. Security breaches in large landscapes is the key problem that SAP ETD is designed to solve, as security threats continue to evolve.
We would like to thank Nicy Thekkethala for her valuable contribution to this article.